These go to 11
Research points to hybrid threats and hybrid warfare targeting the private sector as the most likely form of future conflict in Europe, and that hybrid threats and, implicitly, influence operations, are already prevalent. This article intends to clarify the basics in influence operations and thereby present examples in how influence operations can be projected and amplified in the private and civil sector.
By: Richard Utne & Birgitte Førsund
The reference “these go to 11” is considered the most remembered scene from the mockumentary This Is Spinal Tap from 1984, where the guitarist demonstrates amplifiers whose volume knob is marked from zero to eleven, instead of the usual zero to ten (maximum). Believing that this numbering increases the highest volume of the amplifiers, he explains: “It’s one louder.” When the reporter asks why the ten setting is not simply set to be louder, the guitarist hesitates before responding: “These go to eleven.” Reputedly, real bands and musicians started buying equipment with volume knobs going to 11 because of the film.
In modern risk management, the risk perspective of perception is considered a belief (a narrative) held by an individual, group, or society and allows personal affections such as feelings and emotions to reflect their perception of threats and/or opportunities. An example of means to influence public opinion and perception is a synchronized attack package1 with a combination of both kinetic and non-kinetic instruments. The implication of the reference from This is Spinal Tap is a strategy in influence operations to combine different instruments of power to amplify a perception and to create a public narrative.
Influence Operations
There is no clear understanding as to what constitutes the term influence operations. Ironically, influence operations is closely associated with the term hybrid threats, to which experts has stated “the international consensus on ‘hybrid warfare’ is clear: no one understands it, but everyone, including NATO and the European Union, agrees it is a problem”.2
So-called hybrid threats and hybrid warfare is considered as a combination of kinetic (conventional) and hybrid (non-conventional) instruments of power. Despite domination of non-conventional force in hybrid warfare, hybrid warfare also includes projection of kinetic threats, e.g. assassinations (Figure 1). Initially, in the categorization of hybrid threats, cyber threats can be distinguished from cyber operations in:
a) The operation domain, as malware to critical infrastructure
b) The information domain, to create a narrative in support of the operation and/or to influence decisions or opinions3
Here, we focus on the combination of kinetic and non-kinetic instruments of power as amplifiers for influence operations.
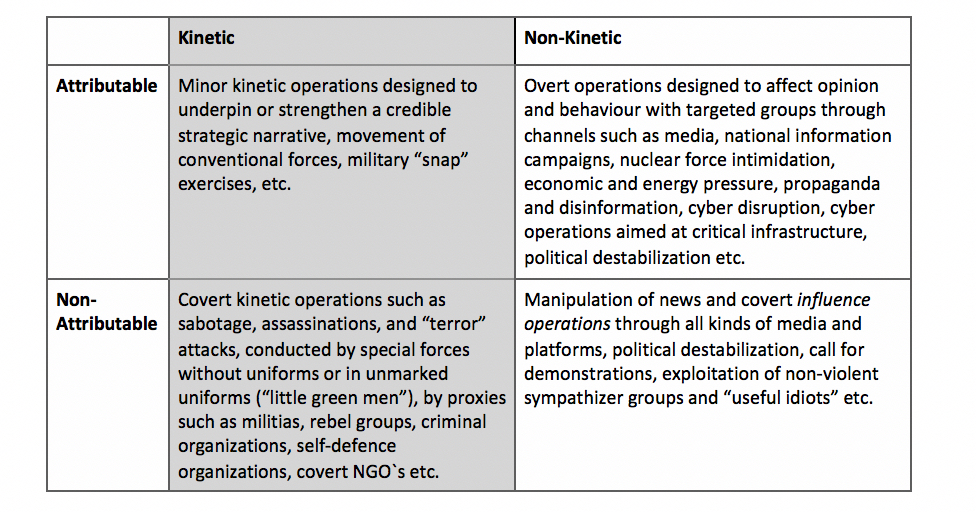
Figure 1: Categorization of hybrid threats.4 The figure shows that influence operations can be projected by both kinetic and non-kinetic hybrid threats, and are represented by attributable and non-attributable instruments of power; military, political, economic, civil and information (MPECI) .5
Hybrid warfare can be perceived as a phase where the frequency of hybrid threats over time surpasses a baseline of what can be considered as single events, but with no clear definition to what level of effect they cause to a societal critical infrastructure’s basic functional ability,6 to distinguish them apart from the “regular noise”. To understand the differentiation of hybrid threats and hybrid warfare, there are two terms that can cause confusion because they seem to be alike; MPECI and PMESII. Figure 2 illustrates that hybrid threats are those posed by an adversary by Military, Political, Economic, Civil, Information (MPECI) instruments. These factors are referred to as instruments of power7 which can be utilized in order to create both horizontally and vertically escalation (figure 2) and are likely to include a wide variety of interventions and operations as shown in figure 1.
A synchronized attack package (SAP)8 targets our societal vulnerabilities across the Political, Military, Economic, Social, Information, and Infrastructure (PMESII) spectrum and is also associated with the concept of hybrid warfare, or, low-intensity conflict. Influence operations with a strategic objective to own the narrative, to shift the strategic centre of gravity in favour of an adversary, is likely to be an important element in hybrid warfare. Thus, influence operations need to focus on specific vulnerabilities of the society, often as a result of, or as a part of, prolonged espionage and knowledge, or, probing societal vulnerabilities.
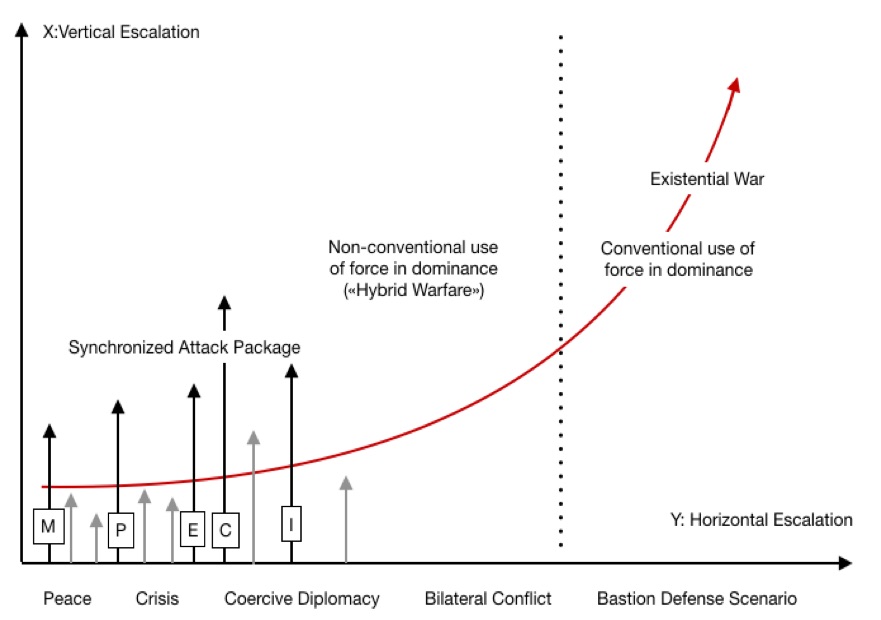 Figure 2: The Synchronized Attack Package (black arrows) is intended to illustrate how hybrid threats can be hard to distinguish from “normal” unwanted incidents (grey arrows). Hybrid threats can be applied across the entire peace/war spectrum and escalated both vertically and horizontally.
Figure 2: The Synchronized Attack Package (black arrows) is intended to illustrate how hybrid threats can be hard to distinguish from “normal” unwanted incidents (grey arrows). Hybrid threats can be applied across the entire peace/war spectrum and escalated both vertically and horizontally.
The Security Policy Dimension of Influence Operations
In Norway, the most important critical social functions are governance and sovereignty, the security of the population and the functionality of society. Implicitly, these critical social functions are also subjecting that, if dysfunctional, they can erode the public’s confidence in the government’s ability to safeguard the population. Subsequently within the critical social functions there are various types of supplies and infrastructure-based services that serve the population, which at the same time constitute input factors for businesses that are responsible for other critical societal functions. Failure to function in this category can propagate to other parts of society. Examples here are failures in the supply of electricity that can result in effects such as water and wastewater loss, disruption of financial services and electronic communications etc. and presents significant challenges for the health and care sector and for crisis management. Serious failure of functions in this category can create social unrest and problems in everyday life with consequences for people’s safety and cause effect to important societal interests.9
Cyber attacks that cause damage, destruction, or disturbance to the private sector are still relatively rare, but “the cyber threat” and digital attacks against critical infrastructure are considered a rapidly growing concern. However, in 2018 a report from the Norwegian Defence Research Establishment (FFI) concluded that the perception of the cyber threat as a crucial factor in conflicts, to permanently paralyze an opponent with spectacular digital attacks on societal infrastructure, is hardly realistic.10 Instead, the cyber threat must be seen as an instrument of power projected in conjunction with other coordinated events, where the main objective is to win dominance of the information domain, to own the narrative and shift the centre of gravity in favuor of not reaching a consensus for reprisals, or, to identify the level of maturity in contingency, to what level governments identify imperative obligations to protect societal resilience (i.e. as a part of prolonged espionage).
A synchronized attack package, where effects from multiple instruments of power are accumulated, is in sum considered to deliver greater cost-effective societal damage than the effect of a single conventional attack. An example can be a malicious malware attack on a power plant to create a power outage. Its effect can be amplified in synergy with (say) extreme temperatures. Vulnerable groups of the population will in such scenario create need for resources, especially within groups such as home-care and the elderly. Combined with a disinformation campaign, social media can provide a platform for amplification of distrust to a government. Creating a false narrative about a government (which has been) ignoring this population and raise demand for political change. A narrative can be created by populating and repeating a message until it hits cracks in the fabrics, for example, by turning coins on populistic beliefs, i.e. “us and them”.
In social media, this strategy is often referred to as microtargeting, where influence accounts join existing social circles and only engage with a few different people, or, influencer influencing, where these accounts only try to affect a few proxies, either journalists or other influencers, who can carry their message for them.11 Here, the strategic narrative can be amplified with various instruments of power adjusted to the level of observed effects.
In the 2019 political elections in Norway`s fifth largest town, Kristiansand, a Facebook-page founded with resources to finance continuous activity likely shifted the political landscape in favour of a minor opposition.12 Although this example is not linked to hybrid threats, it serves as an example to show how social media can help amplify a message. Despite the oppositions far-right program, they placed themselves close to all major parties, claiming willingness for cooperation (“we come in peace”). Such deliberate positioning can affect democratic and consensus-based decision-making environments because they are predictably based on the position of the median voter and influencing this group will thus likely be the most desirable strategy to maximise effects in political campaigns.13 In Kristiansand, the narrative from the Facebook-campaign was likely amplified due to three major political, civil and economical events in real-time; a major infrastructure project, a public investment in an art centre and a controversial relocation of the city`s main port.
In October 2019, in his proposition for the Norwegian armed forces long term plan, the Norwegian Chief of Defence called for a historic investment in re-building capacities. And despite the distance between the left- and right-wing parties, the message has been met with consensus throughout the government. But the parties may also have different motives to support. While some parties want to show the NATO-alliance that Norway is stepping up to meet the 2%-target, others believe that this is a right step to succeed without being dependant on Allied support. Thus, resistance to change does not need to come from outside, but the inner resistance can be cultivated.
This issue concerning cultivation and political influence challenged the area of concern in the 2017 Exercise Forgotten Waters from The Centre for a New American Security (CNAS). The exercise exposed the players involved to their lack of familiarity with hybrid threats, especially in relation to the geopolitically important North Atlantic passage between Greenland, Iceland and the United Kingdom, known as the GIUK-gap. In the exercise, players were told that a disinformation campaign in Iceland had altered the outcome of the country’s national election, putting a government into power intent on reducing the U.S. military presence in Iceland. In the exercise, the players faced a string of complicated challenges: the need to expose and counter disinformation campaigns, the need to maintain and fortify NATO-alliance unity, and the need to develop alternative base options for the U.S. P-8 Poseidon maritime patrol aircraft. The exercise showed the participants how influence operations affecting the internal politics of a NATO ally could create a great concern to the security of the Alliance, presenting this level of complexity in order to address the transatlantic unity necessary to respond with swift decisions and effective counter-measures.14
How is the private sector affected and how do we increase ability to detect influence operations and react?
Today, the resources and critical infrastructure that are important components for critical social functions are in many cases owned and operated by the private sector, and research points to hybrid threats targeting critical infrastructure, the civil society and the private sector as likely to be a key factor in any future conflict in Europe.15
In March 2019, the Norwegian Business and Industry Security Council (NSR) presented a study on hybrid threats targeting the Norwegian business community. The study, which included 354 interviews from Norwegian businesses in the public and the private sector with 100 or more employees, found that:
- 67 percent of businesses believed that having a central and well-established position in society makes them potential targets of hybrid threats
- 70 percent of the businesses believed a lack of ability to recognize attempts at influencing their operations camouflaged as other inquiries constitute a condition that makes the business vulnerable to hybrid threats16
The findings reflect that protecting critical infrastructure is largely a responsibility that imposes on the private sector itself, rather than public responsibility in the traditional sense. This is an important aspect of how influencing operations affect the private sector, because, notably, 63 percent of the businesses in the study believed their vulnerability to hybrid threats was due to lack of situational awareness of hybrid threats to the organization.
In 2017, the NotPetya ransomware was directed at the Ukrainian Government. From Ukraine the virus spread to private entities, among these the Copenhagen-based shipping giant A.P. Moller-Maersk and Mondolez. This example show that to what constitute countering hybrid threats to private businesses is largely a responsibility that imposes on the private sector itself, rather than military preparedness in the traditional sense. A news article pointed out, that those who launched NotPetya did not declare war on the Ukrainian government, and neither did Russia in the invasion of the Crimean Peninsula. Actually, the article noted, most armed conflicts since World War II have not included declarations of war at all.17
How is this a concern to private businesses in particular? An example is Zurich, a global leading insurer, which claims the NotPetya to be an act of war while one of its customers, Mondolez, argues the opposite. The reason for discussion is that Mondolez lost millions of dollars due to NotPetya. Now, the private companies are arguing the definition of war and responsibility for insurance pay out in court.
Hence, influence operations can be designed to be non-attributable, to stay under detection levels of abnormality and may appear in a pace designed to stay below thresholds that normally would raise awareness to shifting conditions and challenges the traditional bipolar perception of peace or war.
“There’s a feeling among many states that other states are carefully calibrating their cyber-aggressions, so they fall below the threshold of war,” said Gary Brown, a former U.S. Air Force judge advocate who now teaches cyberlaw at the National Defence University in Washington. “That makes it challenging for the targeted country to respond. It’s neither war nor peace—it’s constant competition.”
– Elisabeth Braw: Can Courts Clear the Fog of War? (Foreign Policy, 2019)
How quickly do we get so used to the unusual, that the unusual becomes normal? Have amplifiers affected our perception of the narrative? Have GPS disruptions in the High North gradually become so common that we no longer raise an eyebrow to these reports? What about other countries’ military presence near our waters? What about cyber attacks on our healthcare system? When did phishing attempts at your workplace become normal? And what about the things we do not see? Unexplainable diseases which disappears as quickly as it arises and only within a country`s borders?
In a constantly shifting world it can be challenging to identify a deviance from what is normal, when our reference to what is normal is constantly shifting and all parts of the societal safety system is being affected. The parable of the boiling frog is often used to explain why humans react quickly to new events but fail to react to slowly changing conditions until it is too late: If you are a frog, you jump from a pot of boiling water. But if you are placed in a pot of tepid water that is gradually heated you fail to react and will eventually die.
Accordingly, because of the high degree of plausible deniability associated with influence operations, perceived anomalies in the PMESII spectrum should balance uncertainty with trust founded in the precautionary principle, which implies public responsibility to (re)act when there is a plausible risk to critical social functions. A Norwegian Public Inquiry (NOU 2019: 13) is now on hearing for statements on a new law that can provide cross-sectoral power of attorney in peacetime, where extraordinary situations may arise, where there is a need to act quickly and where current legislation does not provide enough flexibility. Hybrid threats and dysfunctions to critical infrastructure are examples of events where this law is considered relevant. However, to what level critical societal functions need to be affected, and whom to decide what level of threshold values to be exceeded cross-institutional wise, remains open. An obvious challenge for response is to reach consensus if there is no obvious threat or adversary, rather a common perception of a phase of peace. One way to improve robustness and resilience for societal safety is thus not limited to mechanisms to counter hybrid threats and influencing operations but includes distribution of knowledge to the system being affected. Then this knowledge can act as sensors for early warning and activate existing preventive mechanisms.
Building resilience today, does not only imply strengthening digital and physical infrastructure, it is thus also about strengthening knowledge and awareness about the threat landscape we have today. Clearly, private business and civil society play an important role in countering influence operations and hybrid threats. The new threat situation also means that old dividing lines between public, private, civil and military are gradually erased and we therefore need cooperation we have not had before across areas of responsibility.
So, how should we make the public and the businesses aware of and report fake news and influence operations? Next year, the Norwegian Directorate for Civil Protection (DSB) oversees an exercise called Exercise Digital 2020 which unites private business, public organizations, civilian approach and the military. There are great expectations of learning opportunities and to identify and develope further measures based on the exercise. Hopefully, it will contribute to increased awareness about the threat picture as well as what measures we should prioritize to prevent against attacks that are aimed to destabilize our society. Security processes ahead should invariably include “everyone” and be incorporated into year-round security processes to be constantly updated according to the threat picture, and as communicated by open threat reports from authorities like Norwegian Police Security Service (PST), Norwegian National Security Authority (NSM) and the Norwegian Armed Forces.
Today, international security policy can just as easily hit a municipality in Norway. For example, as mentioned in the form of hacking of a local power company, which in next turn creates a debate and affects peoples trust and confidence to the government. It is therefore important for all citizens and businesses to have a common understanding about the threat picture. The more aware and responsible each part of a system reacts to anomalies, the more are we able to build a robust society against destabilizing operations. The more knowledge also means increased reporting of suspicious events to authorities and will strengthen the much-needed public and private cooperation we need within security issues like hybrid threats. It also contributes to documentation of a more accurate situation picture of threats and makes it easier for relevant authorities to map events, put them in system and respond with countermeasures.
Knowledge and awareness about hybrid operations and which authority to report to, must be integrated into the societal backbone to react and report, as the mechanisms of whistleblowing in the private sector has worked for years. Knowledge and awareness about hybrid influence operations, fake news and divisive tone of voices should therefore be just as relevant for the private sector as in the Norwegian Armed Forces Situational Center (SITSEN) in Oslo.
Because hybrid threats and influence operations are largely a responsibility that imposes on the private sector itself, rather than military preparedness in the traditional sense, an important challenge on this topic is determining where private responsibility for countering hybrid threats ends, and public responsibility begins.
In the meantime, we risk “these will go to 11”.
About the authors
Richard Utne is Senior Advisor to the County Governor of Agder. He has extensive international experience in risk management and security management, both in the private and public sector. Utne has extensive service experience from the Norwegian Armed Forces and participates in various expert groups related to social security. He has also been a contributor to the Hybrid Survey conducted by the Norwegian Business and Industry Security Council.
Birgitte Førsund is Director of Junglemap working with digital security. For the past 20 years, she has worked as a liaison between security environments and businesses through several public-private projects focused on digital security. Since 2017, Førsund has worked closely with the Norwegian Business and Industry Security Council on behalf of KPMG Cyber and contributed to the work on the “Mørketall” Survey 2018 and the Hybrid Survey 2019.


Footnotes
The picture is from Scott Myers (2017): Great Scene: “This is Spinal Tap”.
- Cullen. P & Reichborn-Kjennerud, E. (2017). Understanding Hybrid Warfare. The Multinational Capability Development Campaign (MCDC) Countering Hybrid Warfare Project (Norwegian Institute of International Affairs, NUPI).
- Ibid.
- Diesen, S. (2018). Lavintensivt hybridangrep på Norge i en fremtidig konflikt (Norwegian Defence Research Establishment, FFI).
- Ibid.
- The US preferred acronym is DIMEFIL: Diplomatic, Information, Military, Economic, Financial, Intelligence, Law enforcement.
- As described in NOU 2019:13: Når krisen inntreffer, section 4.2 – 4.5.
- Cullen. P & Reichborn-Kjennerud, E. (2017). Understanding Hybrid Warfare. The Multinational Capability Development Campaign (MCDC) Countering Hybrid Warfare Project (NUPI).
- Ibid.
- The Norwegian Directorate for Civil Protection, DSB (2016). Samfunnets kritiske funksjoner.
- Diesen, S. (2018). Lavintensivt hybridangrep på Norge i en fremtidig konflikt (FFI).
- Schneier, B. (2019). 8 Ways to Stay Ahead of Influence Operations (Foreign Policy).
- Dagens Næringsliv (10.10.2019). Spillet om Sørlandsnyhetene.
- Hotelling, H. (1929). Stability in competition.
- Smith, J & Hendrix, J. (2017). FORGOTTEN WATERS. Minding the GIUK Gap: A Tabletop Exercise (Center for a New American Security, CNAS).
- Diesen, S. (2018). Lavintensivt hybridangrep på Norge i en fremtidig konflikt (FFI).
- The Norwegian Business and Industry Security Council, NSR (2019). Hybridundersøkelsen.
- Braw, E. (2019). Can Courts Clear the Fog of War? (Foreign Policy).
Norwegian version: Påvirkningsoperasjoner

